Today, I want to talk about something I messed around with recently – a thing called “Matrix Attack”. Sounds cool, right? It kinda is, but it’s also a bit of a headache if you’re not careful.
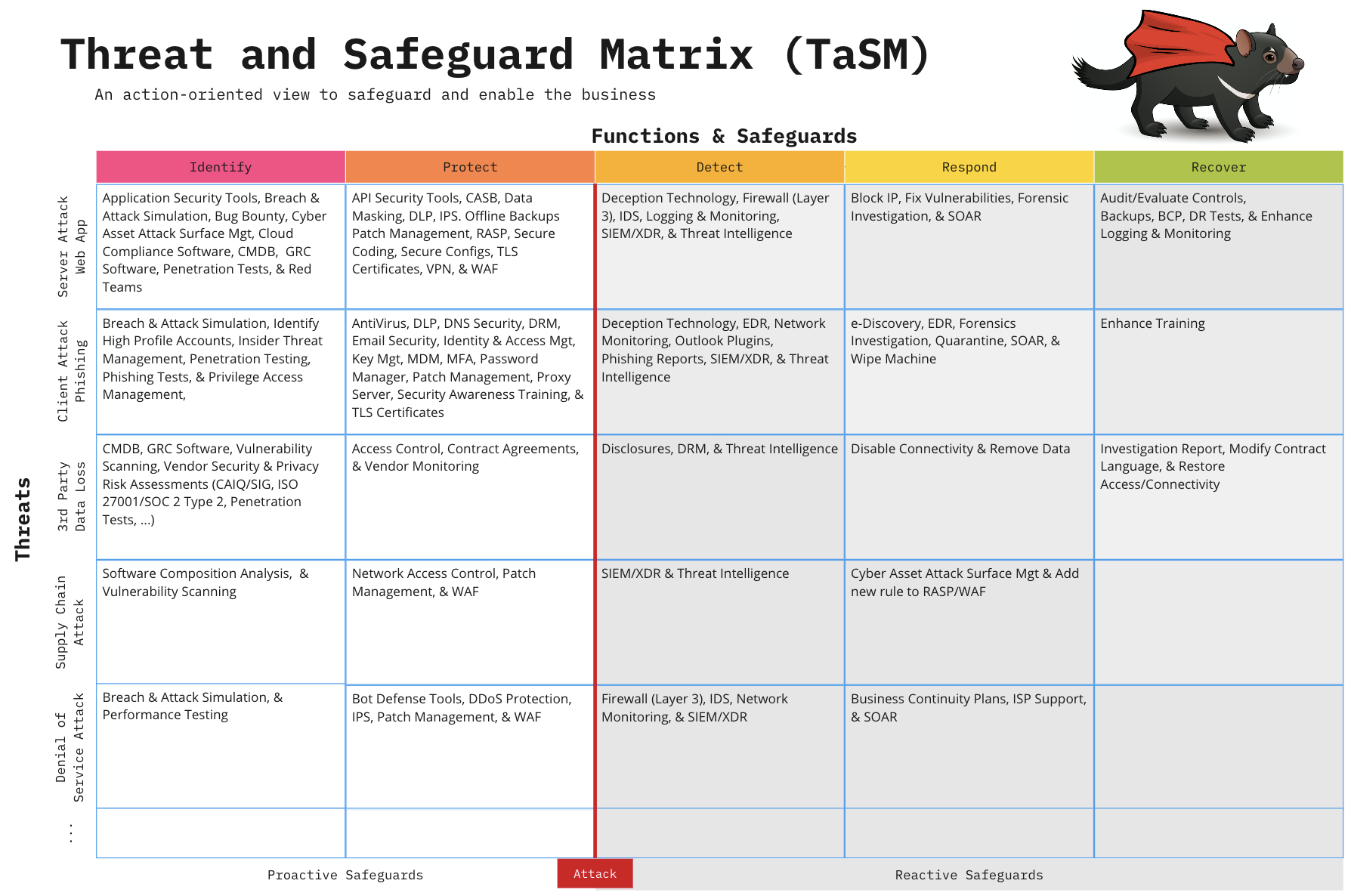
So, I started by just looking up what the heck this thing even was. I found out there are a bunch of different types of these matrix things related to cybersecurity. I saw some people say there were seven types, like “attacker”, “kill chain”, “threat intelligence”, and a few others. I didn’t really know what most of them meant, but it gave me a starting point.
My first step was to play around with those types. I mean that what I do all day, right? I picked one that sounded interesting – “vulnerability”. I figured, that had to be important, right? Everyone’s always talking about vulnerabilities in systems.
Exploring Vulnerability Matrices
I started to make a simple table, a matrix, listing some software I use and then tried to find some known vulnerabilities for them. Let me tell you, it was a rabbit hole! Every piece of software seemed to have a bunch of problems. I used a table like this:
- Software Vulnerability
- Browser Some old bug
- Operating System Another issue
- Some App Yet another problem
Then I was thinking, what’s next after finding these problems? Well, there’s this other matrix type called “exploit”. Seemed like the next logical step. So, I dug deeper. Could I find actual exploits for the vulnerabilities I listed? Turns out, sometimes you can, sometimes you can’t. It all depends on how well-known the vulnerability is and if someone’s already made an exploit for it.
After that, it was time to think about the “impact”. What happens if someone actually uses one of these exploits? I started to add another column to my table:
- Software Vulnerability Exploit Impact
- Browser Some old bug Maybe a script Could steal your cookies
- Operating System Another issue Some code I found Could take over your computer
- Some App Yet another problem No public exploit Maybe nothing, maybe something bad
I did this for a few different things and let me tell you, it gets pretty scary when you start to see how all these things connect. A simple vulnerability can lead to a nasty exploit, which can then have a huge impact.
I didn’t stop there, though. I realized that just knowing about these problems wasn’t enough. What about protecting myself? This got me started on another type of matrix, “attacker”. Who are these people trying to exploit these vulnerabilities? What are their motives? This opened up a whole new can of worms! I did some digging again, and listed a few things I could learn about attackers in another matrix.
Understanding the Attackers
For this part, my matrix started to look like this:
- Attacker Type Motivation Methods Example
- Script Kiddie Showing Off Common Exploits Some kid trying to deface a website
- Hacktivist Political Cause DoS Attacks, Leaks A group attacking a government website
- State-Sponsored Espionage, Sabotage Advanced Persistent Threats Some nation trying to steal secrets
See, I tried to put down some simple attacker types and some examples I thought matched. It really made me think about the different kinds of threats out there.
In the end, messing with these matrix attacks was a real eye-opener. It’s like putting together a puzzle, where each piece is a different part of the cybersecurity picture. You start with a vulnerability, then look at exploits, then the impact, and finally, who’s behind it all. It’s a lot to take in, but it definitely makes you think twice about clicking on random stuff on the internet!
Anyway, that’s my little adventure with matrix attacks. I just wanted to share it in case anyone else is curious about this stuff. It’s a wild world out there in cyberspace, and the more you know, the better prepared you are.



















